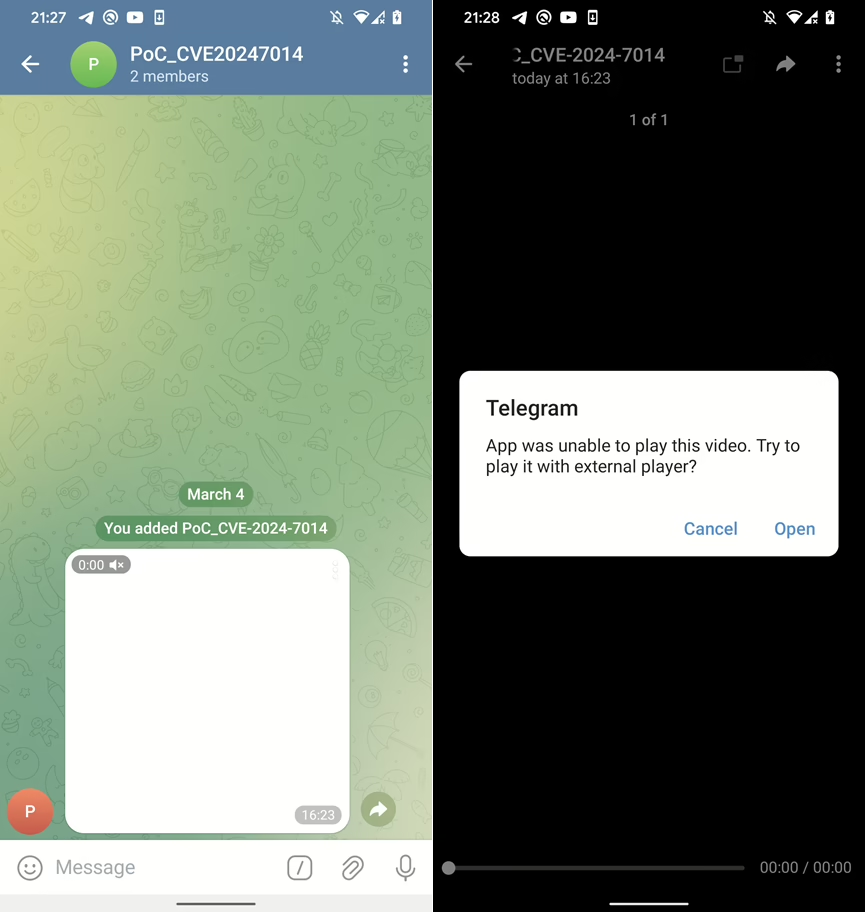
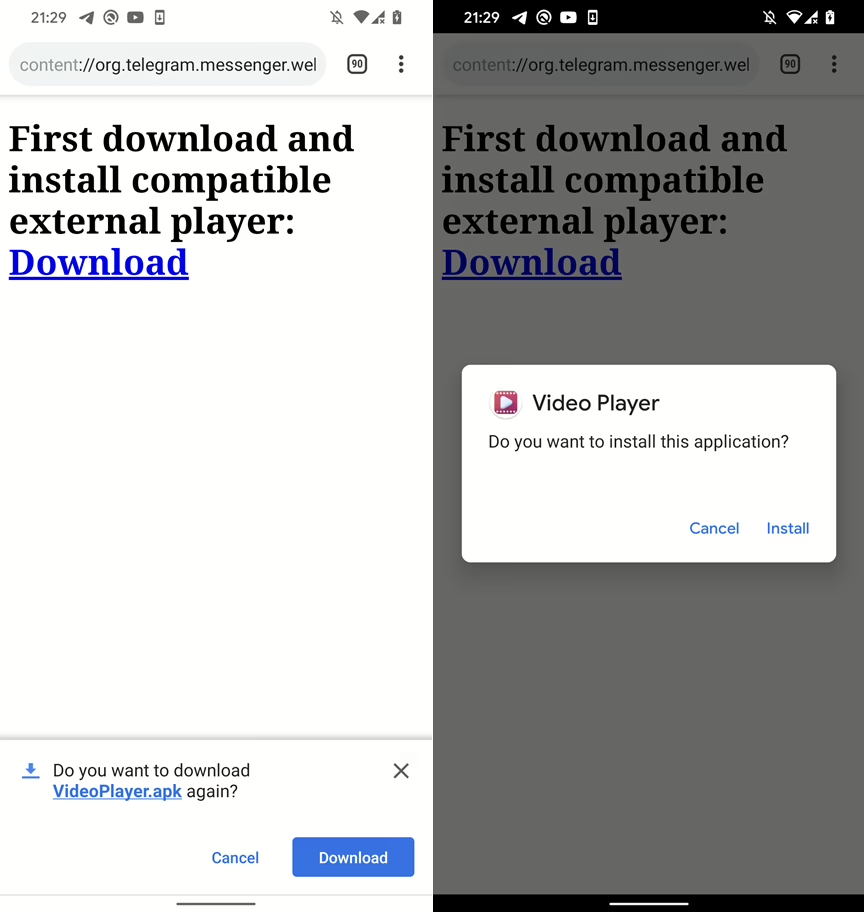
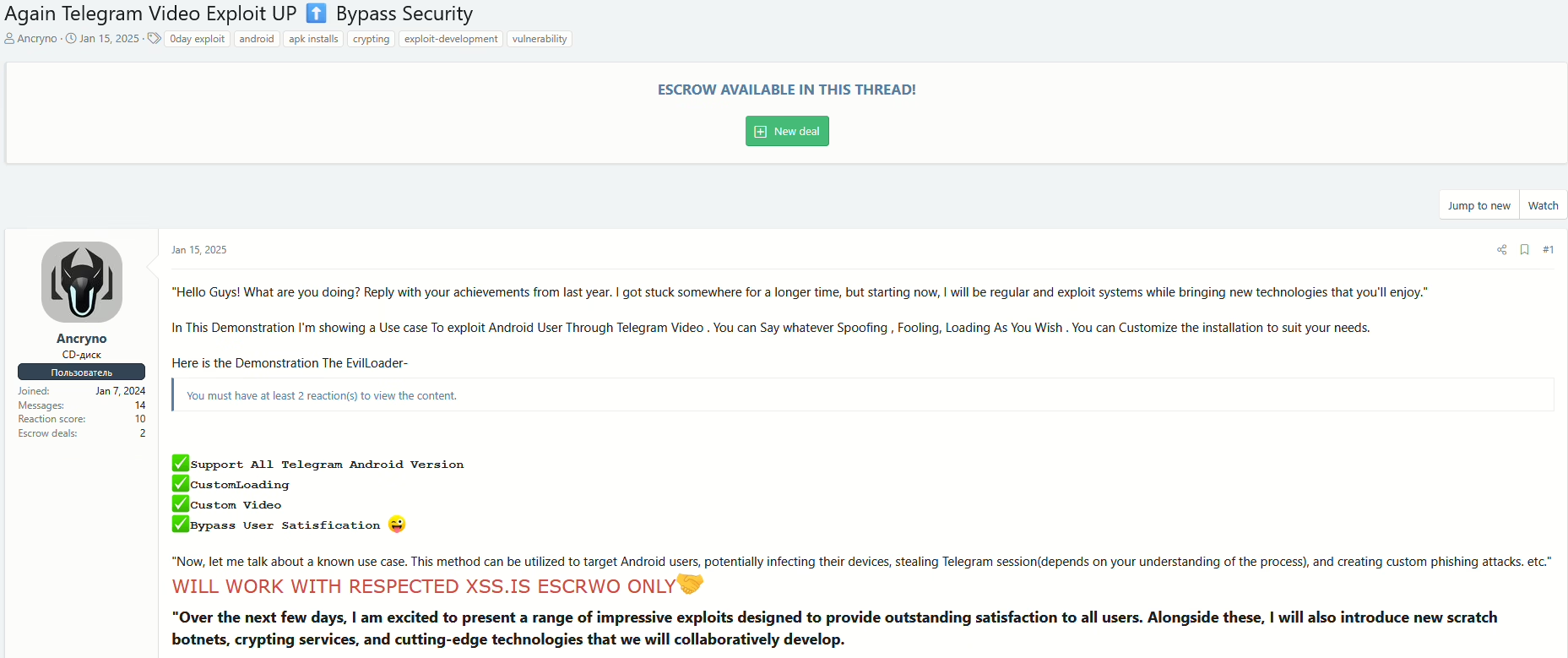
Cybersecurity researchers have shed light on a new campaign targeting WordPress sites that disguises the malware as a security plugin.
The plugin, which goes by the name “WP-antymalwary-bot.php,” comes with a variety of features to maintain access, hide itself from the admin dashboard, and execute remote code.
“Pinging functionality that can report back to a command-and-control (C&C) server is also included, as is code that helps spread malware into other directories and inject malicious JavaScript responsible for serving ads,” Wordfence’s Marco Wotschka said in a report.
First discovered during a site cleanup effort in late January 2025, the malware has since been detected in the wild with new variants. Some of the other names used for the plugin are listed below –
- addons.php
- wpconsole.php
- wp-performance-booster.php
- scr.php
Once installed and activated, it provides threat actors administrator access to the dashboard and makes use of the REST API to facilitate remote code execution by injecting malicious PHP code into the site theme’s header file or clearing the caches of popular caching plugins.
A new iteration of the malware includes notable changes to the manner code injections are handled, fetching JavaScript code hosted on another compromised domain to serve ads or spam.
The plugin is also complemented by a malicious wp-cron.php file, which recreates and reactivates the malware automatically upon the next site visit should it be removed from the plugins directory.
It’s currently not clear how the sites are breached to deliver the malware or who is behind the campaign. However, the presence of Russian language comments and messages likely indicates that the threat actors are Russian-speaking.
The disclosure comes as Sucuri detailed a web skimmer campaign that uses a fake fonts domain named “italicfonts[.]org” to display a fake payment form on checkout pages, steal entered information, and exfiltrate the data to the attacker’s server.
Another “advanced, multi-stage carding attack” examined by the website security company involves targeting Magento e-commerce portals with JavaScript malware designed to harvest a wide range of sensitive information.
“This malware leveraged a fake GIF image file, local browser sessionStorage data, and tampered with the website traffic using a malicious reverse proxy server to facilitate the theft of credit card data, login details, cookies, and other sensitive data from the compromised website,” security researcher Ben Martin said.

The GIF file, in reality, is a PHP script that acts as a reverse proxy by capturing incoming requests and using it to collect the necessary information when a site visitor lands on the checkout page.
Adversaries have also been observed injecting Google AdSense code into at least 17 WordPress sites in various places with the goal of delivering unwanted ads and generating revenue on either a per-click or per-impression basis.
“They’re trying to use your site’s resources to continue serving ads, and worse, they could be stealing your ad revenue if you’re using AdSense yourself,” security researcher Puja Srivastava said. “By injecting their own Google AdSense code, they get paid instead of you.”
That’s not all. Deceptive CAPTCHA verifications served on compromised websites have been found to trick users into downloading and executing Node.js-based backdoors that gather system information, grant remote access, and deploy a Node.js remote access trojan (RAT), which is designed to tunnel malicious traffic through SOCKS5 proxies.
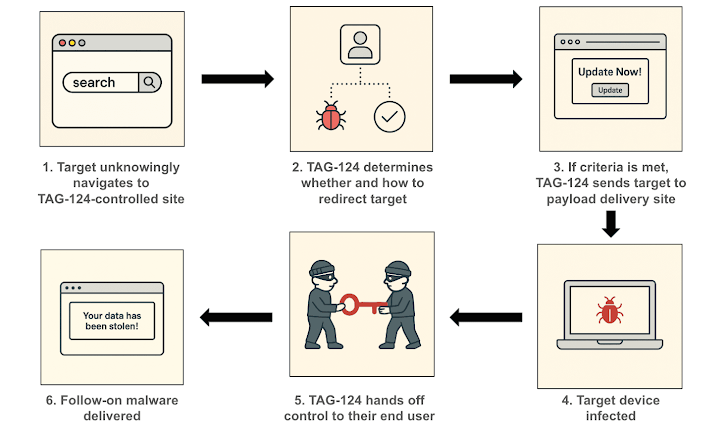
The activity has been attributed by Trustwave SpiderLabs to a traffic distribution system (TDS) called Kongtuke (aka 404 TDS, Chaya_002, LandUpdate808, and TAG-124).
“The JS script which, was dropped in post-infection, is designed as a multi-functional backdoor capable of detailed system reconnaissance, executing remote commands, tunneling network traffic (SOCKS5 proxy), and maintaining covert, persistent access,” security researcher Reegun Jayapaul said.
Found this article interesting? Follow us on Twitter and LinkedIn to read more exclusive content we post.